Steam'deki Chemia, Oyun Güncellemelerinde Kötü Amaçlı Yazılımları Gizliyor
A mysterious Steam game called Chemia is being used to quietly distribute malware through its updates, researchers say. The game, available only through request-based early access, is connected to a known hacker group, and it’s now the third known incident of malware getting onto the platform. With weak screenshots, no public developer presence, and a stealthy executable buried in its files, Chemia is looking more like bait than an indie survival game. And while Valve hasn’t responded publicly yet, the way this and earlier incidents played out shows that Steam’s current defenses aren’t keeping malicious games off the store.
Cybersecurity researchers at Prodaft say the Chemia situation involves more than just shady devs. According to their report, the game is being used by a hacking group known as Larva-208 (also referred to as EncryptHub). The group has allegedly injected two known types of malware into the game: Fickle Stealer and HijackLoader. These are triggered when users download and launch the game, running in parallel with the software itself. And although Chemia is locked behind a request-based access system, it’s still live on Steam.
“When users download and launch the game, the malware executes alongside the legitimate application,” Prodaft wrote.
That quote, posted on Prodaft’s GitHub, came alongside a breakdown of what’s actually happening in the game’s files. The researchers say that on July 22, the hackers added a file called
CVKRUTNP.exe
into Chemia’s build. This file works as HijackLoader, and its job is to silently bring in even more malware, like Vidar, which is designed to steal personal information and browser data from infected users.
Chemia is supposedly the work of “Aether Forge Studios,” a developer that doesn’t have a website or any real online footprint. The Steam listing itself is vague, describing Chemia as a survival crafting game. But the only visuals available show generic, low-effort backgrounds—no characters, no UI, no gameplay. The current theory is that the game was set up as a Trojan horse, offering the bare minimum needed to appear real and get listed on Steam.
This isn’t the first time hackers have exploited Steam’s distribution system. In March, another incident involved an upcoming FPS called Sniper: Phantom’s Resolution. In that case, the hacker didn’t put malware directly in the Steam build. Instead, the game’s page linked to an external site with a fake demo. That domain
sierrasixstudios.dev
was featured on the official page, but the real devs hadn’t bought it yet. A scammer registered the domain, uploaded malware, and tricked people into downloading it through file-sharing links.
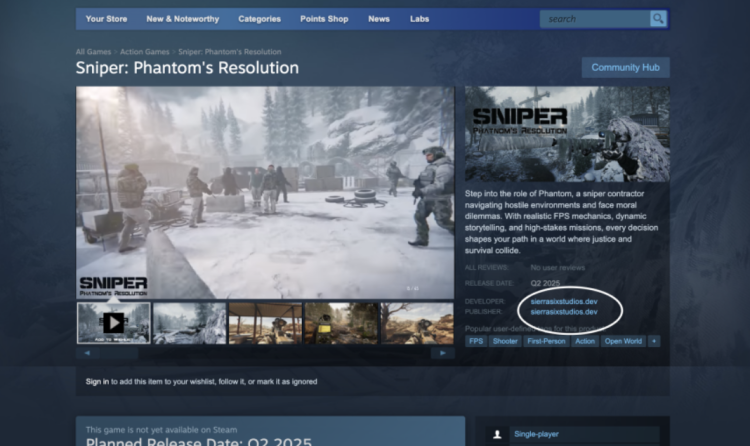
The actual studio behind Sniper: Phantom’s Resolution confirmed that they got caught in the middle of it. A rep named Andrew explained the mistake in a Reddit post, saying the team had planned to build a real website eventually, but didn’t expect anyone to snap up the name so quickly. Once the malicious files were discovered, Valve took the Steam page down.
Earlier this year, another game called PirateFi also slipped through Valve’s safeguards. That one was a free-to-play title uploaded directly to Steam, and it also contained malware. The hacker promoted it on Telegram, using bot messages and even fake job offers for “moderator” roles to lure people in. It’s not clear how PirateFi got past Steam’s backend checks, and Valve didn’t offer details publicly. But the game was pulled once it was flagged.
The difference with Chemia is that it’s a more direct attempt. The malware is part of the game itself and distributed through Steam’s official delivery system. That means the hackers didn’t need a fake website or outside links—they just pushed an update. The presence of the backup malware downloader inside the files shows how this setup works: one click installs the game, which installs the payload, which brings in even more malware.
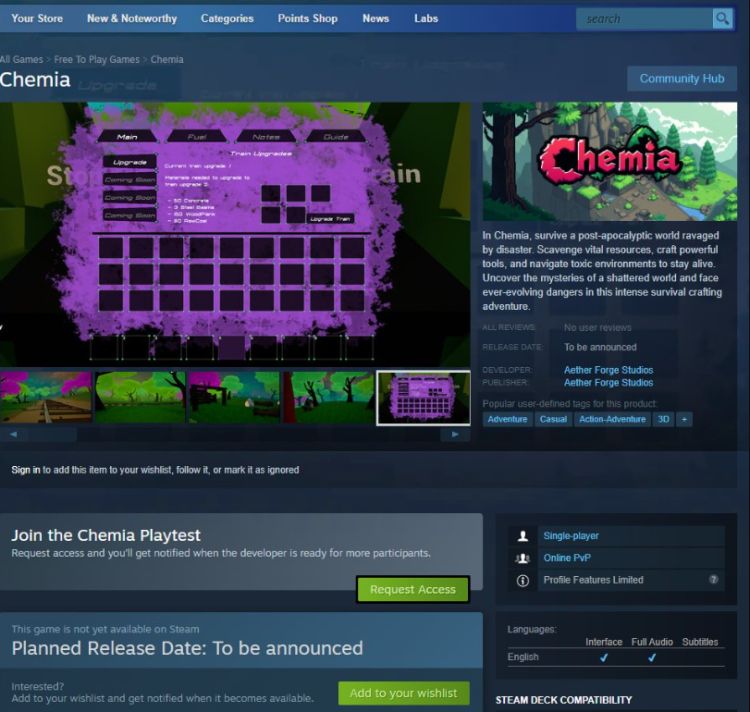
So far, Valve hasn’t made a public statement about the Chemia case. The game remains request-only, so it’s likely that very few users installed it. But that limited reach doesn’t change the fact that this is the third known malware-related incident involving Steam in less than six months.
All three attacks followed slightly different tactics. PirateFi used internal uploads, Sniper exploited an external domain link, and Chemia is pushing infected updates straight through the platform. That variety is a problem for Valve, since it shows attackers are testing different ways to slip past platform security.
Prodaft's public breakdown includes a full list of file names, domains, and malware signatures linked to Chemia. These indicators of compromise are meant to help antivirus vendors and IT admins flag infections. For average users, though, there’s not much to do except avoid unknown games, especially those that require special requests to access, or come from developers with no online presence.
Prodaft didn’t say how long Chemia had been listed before the malware was added. The first signs of foul play showed up with the "CVKRUTNP.exe" file on July 22, but that may not have been the game’s first update. If anyone installed the game earlier, it’s unclear whether they also received earlier builds of the malware. Read also about how Steam cracks down on adult games with a new vague rule, which we've covered in the previous text.
The core issue is trust. When a game appears on Steam, people assume it has passed a basic check. And Valve’s current system clearly isn’t catching everything. For now, the only real filter is user reports and third-party research like Prodaft’s. As attackers get more creative, that gap could widen.

Yorum